The Problem
Microsoft is introducing Strong Certificate Mapping Enforcement to address vulnerabilities in Active Directory’s certificate-based authentication.
Starting with the February 2025 Windows updates, domain controllers will require that any certificate used for client authentication include a secure mapping to its user account – specifically by embedding the user’s Security Identifier (SID). This change (outlined in KB5014754) aims to prevent attackers from spoofing identities with certificates by enforcing a stricter mapping.
Previously, certificates were mapped to users via attributes like UPN or subject name, which is now considered a “weak” mapping. Under the new enforcement, only “strong” mappings (explicit mappings or a matching SID embedded in the certificate) will be accepted for Kerberos logon.
For enterprise mobility, this is especially relevant to Kerberos authentication on mobile devices. Hypergate Authenticator (which enables Kerberos SSO on Android) relies on user certificates to obtain Kerberos tickets. These certificates are typically issued via an MDM (like Ivanti Neurons, MobileIron, etc.) using SCEP or similar, and these do not yet include the AD SID. Microsoft’s enforcement means that, by default, such mobile certificate-based logins will start failing once full enforcement is active, unless updates are made. In other words, Kerberos authentication for mobile clients (Android, iOS, etc.) using certificate-based login will break if the certificates aren’t updated.
This will affect the following Windows Server Versions:
- Windows Server 2025
- Windows Server 2022
- Windows Server 2019
- Windows Server 2016
- Windows Server 2012 R2
- Windows Server 2008 R2 with ESU
And all MDM/UEMs like (version independent):
- Microsoft Intune
- Ivanti Neurons, former MobileIron Core/Cloud
- Omnissa Workspace One former VmWare AirWatch
- BlackBerry UEM
- Soti Mobicontrol
- Samsung Knox
Microsoft allowed a transition period in “compatibility mode” (logging warnings but not blocking auth), but as of February 11, 2025, strong mapping becomes the default, and by September 10, 2025, compatibility mode will be phased out entirely.
Impact on Hypergate Authenticator
In current MDM deployments, Android users running Hypergate Authenticator obtain a user certificate (pushed via MDM) and use it for Kerberos (PKINIT) authentication. Without strong mapping, these logons are currently only succeeding due to compatibility mode, and they generate warnings on your domain controllers. Once strong mapping is strictly enforced (latest in September 2025), any certificate without the proper SID binding will be rejected, preventing mobile users from authenticating to intranet services via Kerberos.
Concretely, a user certificate deployed by your MDM today typically contains the user’s UPN in the Subject or SAN, which Active Directory maps to the account. Under strong enforcement, the KDC will demand a secure mapping (either an explicit altSecurityIdentities mapping in AD or the embedded SID extension). If the certificate lacks the SID, the KDC will refuse to issue a TGT. This means Kerberos SSO sessions (via Hypergate Authenticator) will start failing. Microsoft explicitly calls out that certificates issued via an MDM or NDES (which use “offline templates”) are at risk, and authentication failures are likely if these certificates do not meet the new standards. In short, your mobile workforce could suddenly lose access to Kerberos-authenticated resources if no action is taken.
Errors to expect
Below are examples of the errors you may encounter due to this issue:
-
Windows Event Viewer (Domain Controller, KDC) – Event ID 39 (Warning or Error):
“The Key Distribution Center (KDC) encountered a user certificate that was valid but could not be mapped to a user in a secure way (such as via explicit mapping, key trust mapping, or a SID)…”.
This indicates the certificate presented did not have a strong mapping (no SID extension or explicit mapping). In compatibility mode this is logged as a warning while allowing the login; in full enforcement mode it will be an error and the login is rejected.
-
Windows Event Viewer (Domain Controller, KDC) – Event ID 41 (Error):
“The Key Distribution Center (KDC) encountered a user certificate that was valid but contained a different SID than the user to which it mapped. As a result, the request involving the certificate failed.”
This means the certificate had a SID, but it did not match the SID of the target user account (a secure mapping check failed). The authentication is denied for security reasons. -
Kerberos Client Logs (Hypergate Authenticator): In verbose Kerberos logs (or Hypergate debug logs), you’ll see an error like “Received error from KDC: … Certificate mismatch” when attempting to acquire a TGT.
For example, a
kinitattempt might outputKDC_ERR_CERTIFICATE_MISMATCH. This corresponds to the above event on the KDC – essentially the domain controller saying “I can’t accept this certificate for the user.”
These errors make it clear that the certificate’s account mapping is not considered secure. The SID extension requirement is the key to resolving them. Next, we’ll walk through how to address this in an MDM/UEM environment with Hypergate.
Solution
To ensure continuity of mobile Kerberos SSO, there are two approaches: you can either enable the compatibility mode and later update the certificates, or you can update the certificates directly.
Ultimately the goal is to update the certificates latest by September 2025 so that all Kerberos client certificates carry the proper SID mapping.
Temporary Workaround: Enable Compatibility Mode on Domain Controllers
As an immediate mitigation, enable Compatibility Mode for certificate mapping on all domain controllers. This will allow authentication to continue with “weak” mapped certificates until you update them, preventing outages before the deadline. Microsoft’s guidance is to set a registry key on each DC:
-
Registry Path:
HKLM\SYSTEM\CurrentControlSet\Services\Kdc -
Value Name:
StrongCertificateBindingEnforcement(REG_DWORD) - Value Data:
1(for Compatibility mode, where certificates without SID are still allowed but logged)
Possible values are:
0– Compatibility mode: Disables strong certificate mapping check. Not recommended because this will disable all security enhancements. (no longer possible after February 11, 2025)1– Compatibility mode with Warnings: Checks if there is a strong certificate mapping. If yes, authentication is allowed. Otherwise, the KDC will check if the certificate has the new SID extension and validate it. If this extension is not present, authentication is allowed if the user account predates the certificate.2– Strict enforcement: Checks if there’s a strong certificate mapping. If yes, authentication is allowed. Otherwise, the KDC will check if the certificate has the new SID extension and validate it. If this extension is not present, authentication is denied.
Setting this to 1 ensures the DCs remain in the compatibility (log-and-allow) state. (A value of 2 is Full Enforcement – log and reject non-SID certs – which will become the default after the updates, and 0 would disable the new checks entirely, which Microsoft has already removed in earlier updates. No restart is required for it to take effect.
You most probably also need to consider the CertificateBackdatingCompensation registry key as well. This key addresses a specific case where a certificate’s issue date is earlier than the user account’s creation date (which the KDC views as suspicious). In compatibility mode, by default the KDC only allows a 10-minute difference:
-
Registry Path:
HKLM\SYSTEM\CurrentControlSet\Services\Kdc -
Value Name:
CertificateBackdatingCompensation(REG_DWORD) - Value Data:
5E0C89C0(hex – omit the 0x to enter the correct value via regedit)
Possible values are (choose a value just above your cert lifetime):
0x5E0C89C0– 50 years0x2EFE0780– 25 years0x12CC0300– 10 years0x9660180– 5 years0x5A39A80– 3 years0x1E13380– 1 years
Enabling this allows older certs to authenticate as a weak mapping within that time offset. Only use this if needed, and remember it only works in compatibility mode and is another temporary workaround.
With compatibility mode on, your users’ Hypergate logins will continue to work through the transition (though DCs will log warnings). This gives you time to implement the permanent fix without disrupting service.
Permanent Fix: Update Certificates with SID Mapping
The long-term solution is to embed the user’s SID into the client certificate that Hypergate (and other services) use, so that the certificate can be securely mapped to the user’s account. This typically means updating your certificate templates and MDM/UEM configuration. We will demonstrate this in an Ivanti Neurons environment:
- Navigate to Configurations, filter for Identity Certificate and select your current Certificate configuration:
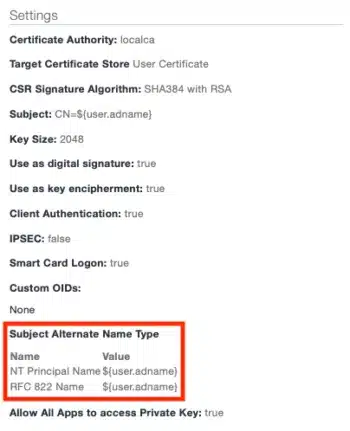
- Add the following additional Subject Alternate Name Type of type Uniform Resource Identifier:
tag:microsoft.com,2022-09-14:sid:${user.sid}– This is a static date – do not change it, the date in it needs to be exactly 2022-09-14.
The correct identifiers are:– Microsoft Intune:
{{OnPremisesSecurityIdentifier}}
– Ivanti EPMM / MobileIron Core:tag:microsoft.com,2022-09-14:sid:$USER_SID$
– Ivanti Neuron / MobileIron Cloud:tag:microsoft.com,2022-09-14:sid:{user.sid}
– BlackBerry UEM:tag:microsoft.com,2022-09-14:sid:%UserSID%
– Soti Mobicontrol:tag:microsoft.com,2022-09-14:sid:$USER_SID$
– Samsung Knox:tag:microsoft.com,2022-09-14:sid:<UserSID> 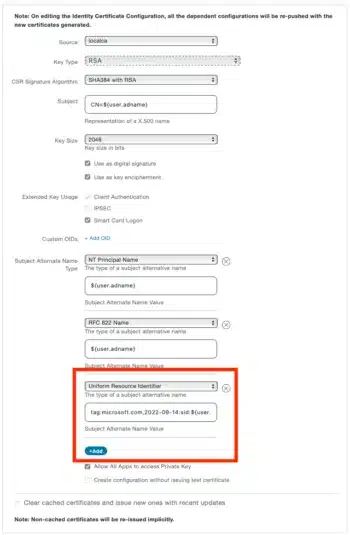
- The Certificate configuration should look like this:
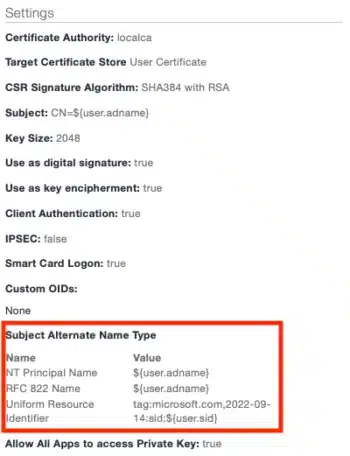
-
This eventually will produce a certificate that will contain the following Subject Alternative Names:
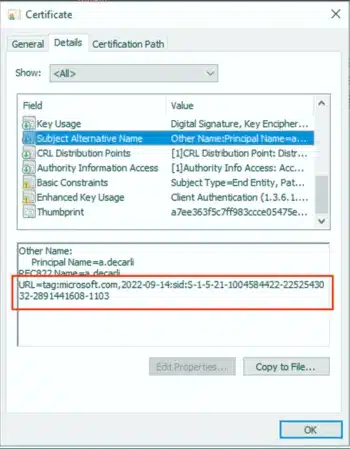
-
Verify the new certificate mapping: After a device receives the new certificate, attempt a Kerberos via Hypergate Authenticator. It should succeed as before. Check your domain controller logs again – you should no longer see Event 39 warnings for that user’s logon. In fact, if the SID is present and correct, the KDC will consider it a strong mapping and won’t log an error.
-
After we verified the certificate mapping successfully, we are now in the position to enforce it. This is only required if we want to enforce strong certificate bindings before September 2025. Afterwards, the registry key is irrelevant and the binding will be enforced anyway. To enable it today, we have to set a registry key on each DC:
-
Registry Path:
HKLM\SYSTEM\CurrentControlSet\Services\Kdc -
Value Name:
StrongCertificateBindingEnforcement(REG_DWORD) - Value Data:
2(for Strict mode)
-
By taking these steps, you’ve implemented a robust solution that meets Microsoft’s new requirements and ensures your enterprise mobile SSO remains uninterrupted. With Strong Certificate Mapping Enforcement in full effect, your Android users can continue to leverage Hypergate for Kerberos authentication securely, and your domain controllers will be satisfied with the strong SID-based mappings on every certificate.