In today’s volume, we will talk about Android Enterprise and its security aspects. A question that a business owner or Chief Technology Officer should ask themselves is how secure is the environment in which employees and sensible data meet. Especially with Mobile Devices.
The data perimeter has moved, the means of accessing business critical information have grown and the threats have shifted focus. The mobile device is now the big target for attackers – and they’re smart enough to take advantage.
You always have to remember the phone is an ‘always on’ device. If you hack a phone, you have access to work and personal information until such a time as the device is disconnected. It’s not the device that hackers are after – it’s the connection the device has to data that is so valuable.
Some facts your company should know about Mobile Security.
- The mobile device is becoming more used than the desktop computer, but in most companies it is less secure.
- Even though they are aware of the risks, companies react often too late
- People assume phones are safer to use. Therefore a lot are more likely to fall victim to a phishing attempt on a phone than on a desktop.
- Attacks are aimed at people and their devices, not companies and their computers.
- Mobile security isn’t just a concern for IT. The way employees use their own devices can have positive impacts on finance, HR and operations. When people can work easily, the output is much better.
- Most employees use the same password for many services. Or they use extremely simple passwords.
More secure than you think
In a previous article, we stated how the Android Operating System is being favoured from businesses, as it offers more flexibility compared to its competitors. Statistics related to this claim can be found in the article: The future of Mobile Enterprise lies in Android. It has been the case in the past that the Android OS has been perceived as inferior in many security aspects.
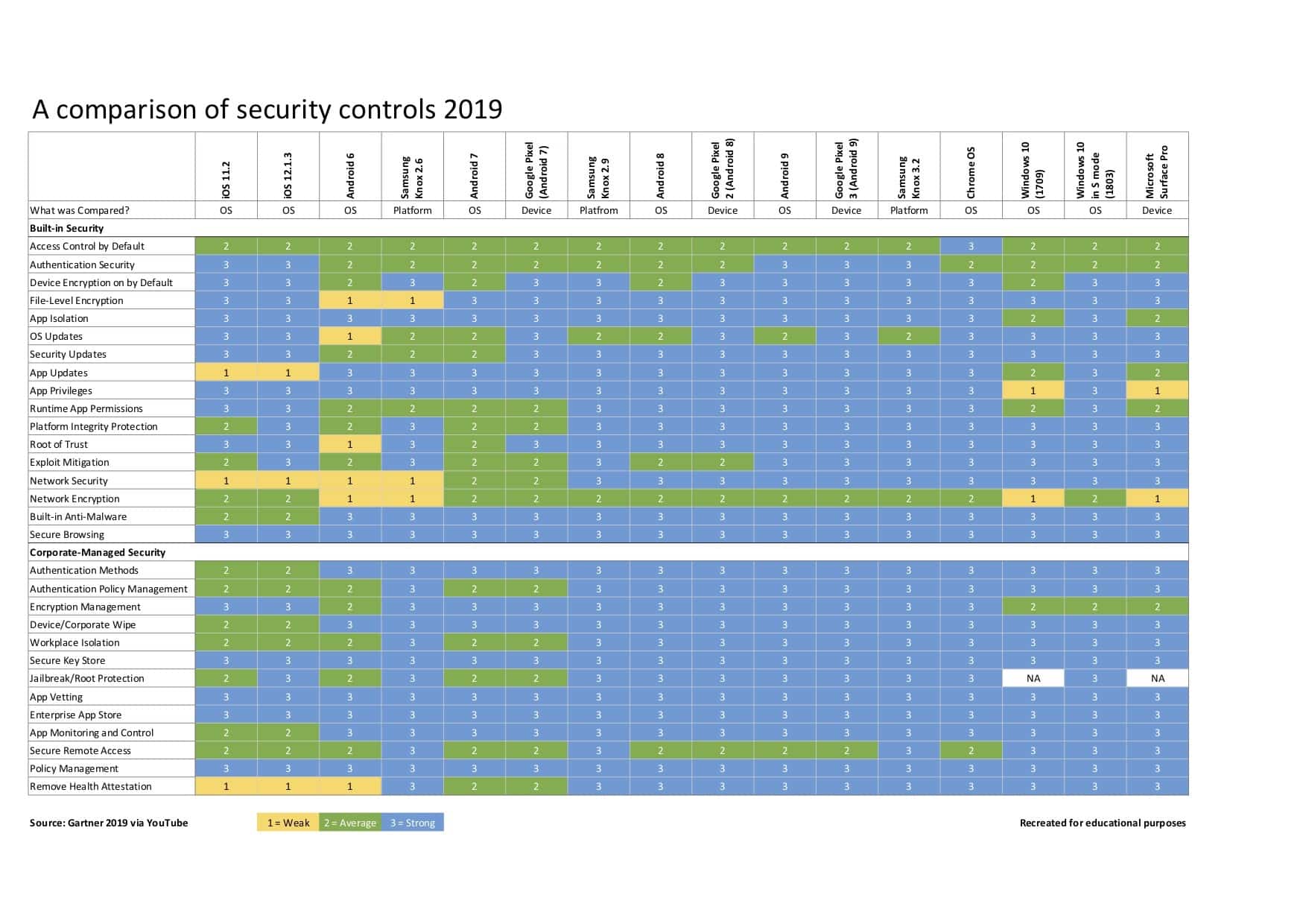
However, since 2016 reports from Gartner have ranked the Android OS as the most secure OS when it comes to personal device aspects such as Built-in Malware protection, Root of trust and File level encryption among others. Now, what should really interest you as a business is Device corporate wipe, App monitoring and control, Authentication methods, and workplace isolation.
The original data form 2019 can be downloaded here. Or have a look at the table below.
Work profile and fully managed devices
There are two main deployment scenarios which are used in the work environment – BYOD or so-called work profile and fully managed devices with work profiles. There has been confusion out there regarding sandboxing; namely, people think that Sandboxing is only available with IOS whereas Android also offers Sandboxing. If you are not familiar with the term Sandbox, it is merely a type of software testing environment that enables the isolated execution of software or programs for independent evaluation, monitoring or testing. This creates a perfect environment to keep infected and corporate data separate.
Before getting into all of the techy stuff, it is essential to understand why it is necessary to take all these precautions when it comes to implementing a BYOD solution for employees.
In the past, we were all worried about the security of our Desktops and Laptops for the lucky ones owning one. These devices were subject to attacks on a daily basis and led to the emergence of software such as Kaspersky, McAfee or Avast.
Nowadays, in a world where Tablets and Smartphones dominate our daily lives, it is impossible for Internet providers to have a 100% configuration of where the threats are. In the business environment, such devices have become the primary use cases for employees on a daily basis.
Attacks on such devices shifted from consumer attacks, namely, phishing for your bank SMS’ where damage would be done to individuals to being able to steal and infect an entire company infrastructure with trojans and malware.
As an employee, how can you be sure that when you walk into the company and connect to the WIFI that there is not a hacker pretending to offer services and stealing all your data, by giving consents.
Not only can such employees be affected in this way but also by hackers stealing developer certificates and creating malicious apps which are installed on phones and monitoring your every move, with you hitting allow when it asks you for permission. The aim of this is not to make you think that you may be having malware or viruses, but to make you aware as to how easy it is for a person with bad intentions to attack your personal “belongings” under your watch.
Down below, you can see an illustration of a possible malware infection.

What is is new security wise in Android Enterprise?
Android has since KitKat version 4.0 grown a lot in the security perspective. They took the secure Linux Kernel as the basis of the android operating system and made it more rigid and secure. As developments happened and Android tried to fix all the endpoint vulnerabilities which consumers were facing they came up with the release of Android 5.0. What was special with this version of the OS was Android for work which today we call Android Enterprise. This allowed organizations to have separate work profiles on devices for their users in a container format.
We have covered in one of our previous post containerizations which is in simple words having one device but two different environments in which one cannot interact with the other. Containerization helps to increase productivity, improves security and makes mobile management cost effective.
Additionally Google created the Google Play Protect which is a set of security controls aiming to scan all applications for malicious content, hence, taking of worries from users about what they would download in the app store. Android or better Google did not only take the precautions on the software side but have also worked along with manufacturers to improve the security of the Hardware. For instance, the addition of the TEE (Trusted Execution Environment ), which is a secure area on the main processor which cannot be altered. Therefore, if one was to have an infected device and the virus wants to boot up a copy of the “Android” Operating system it would not work at all. Storing hashes in the hardware as well as certificates which allow for a less vulnerable device at the end of the day. When moving on android has also started implementing multi-factor authentication both for the personal play space and the workspace. They also have forced encryption on every device. They have also made it possible to quickly push new updates through a monthly security patch, rather than having to update the whole phone when such a security breach was detected.
Looking at the Android architecture and how it is built up it can be split up into six main components. These are listed:
- Applications
- Android framework
- Native libraries
- Android runtime
- Hardware Abstraction Layer (HAL)
- Kernel
Since these components are isolated, running in their own domains, a vulnerability in one component does not compromise the entire system. With capabilities such as verified boot and downgrade protection, these vulnerabilities are also easy to detect now. Similarly, Google’s Play Protect is always on and protects against any known potentially harmful application (PHA).
Up-to-Date
With these advanced features, the importance, awareness and performance of Android Enterprise have significantly increased over the past years. With technological advancements, a proliferation of data has occurred, and there is an ever-growing need now to protect that data. Thus, solutions such as Android Enterprise have a significant role to play in helping organizations to stay up-to-date with the emerging compliance laws and protect employee and consumer data.
Laws and Security
Last year, the General Data Protection Regulation (GDPR) was implemented to protect the privacy of all citizens of the European Union (EU). It aims to protect EU citizens and help them better understand how their information is being used. Not only this, but GDPR emphasizes a lot on the privacy of employee and consumer information, which can be compromised in case of a security breach. Thus, big companies like Google have already publicly committed to comply with GDPR laws. It would be fascinating to see how these new laws are integrated into the current Android Enterprise system. A recent example would be that of Android Q, in which IT admins can now block the installation of apps from unknown resources across the entire device, protecting against malware and a possible data breach.
With advances in artificial intelligence, companies like Google are covering significant ground when we talk about security aspects of Android Enterprise. For example, with Google’s over-the-air update, 60% of security threats are now being detected in real-time. Since systems like Google Play Protect never stop learning, companies and individuals have the latest features in mobile security. Moreover, management APIs allow companies to implement policy controls across their entire fleet of devices. This allows them easy and effortless control over corporate apps and data.
With these advancements, 77 percent of multinational US firms prefer android over iOS. According to IDC Infographic, the main contributing factor is that “Security incidents are less frequent in Android-majority enterprises compared to iOS-majority deployments”.
The popularity of these systems can also be judged by the fact that banks around the world are moving towards android to help them with their mobile-first approach. BYOD programs, along with others, are being integrated into banks and financial institutions as part of Android enterprise solutions. Bank executives believe that since employees can access information on their personal devices, this flexibility has, in turn, increased their productivity. With Android work-profile, employees can use their personal devices to work, knowing that their personal data and apps will not be compromised.
Android Enterprise is the Future
Moreover, android’s multi-layered protection, as validated by Gartner, allow these institutions to easily integrate this technology into their systems as it complies with security laws. The Chief Information Officer at CaixaBank, number one retail bank in Spain, says that this technology has helped the bank with customer service as the employees can help the consumers from any location. Now that this system is thriving in the tightly-regulated financial services industry, analysts believe that it would not be long before it is implemented in every industry, especially the ones where regulations are not that strict.
Considering such popularity, it is not surprising that 78 percent of business phones shipping in 2019 will run Android (according to IDC). With this in mind, it will be interesting to see what the future has in store for this technology – fortunately, a summary of the future was discussed at Google Cloud Next’19:
Android Enterprise Recommended was discussed at the meeting, which is a Google backed program which is making it easier to manage Android devices across any organization. Google is also striving to ensure that devices and data are more secure than ever before; the company is doing so through enterprise-grade protections and controls. Most importantly, new updates in Android Q have incorporated a lot of feature requests – a prominent one is an API that allows consolidation of personal and work calendars and enables separate input for work and personal apps.
These efforts by Android spring out of a need to stay relevant in the market and international regulation that reprimands negligence to security with monetary and other penalties. While interconnectedness makes workflow smoother, it also allows an opportunity to launch an attack that could spread exponentially throughout all the devices and applications that are connected.
Data is king
In today’s era, data has become one of the more valuable assets, making OS service providers custodians of a commodity that gives its holder insights into sensitive information: demographics, behaviour patterns, personal preferences, etc. A responsibility of this nature requires the party in discussion to take any and every step possible to mitigate risk and ensure secure store and smooth transfer of information.
In the past, we have seen how negligence in maintaining and improving security protocols surrounding data stored on devices can lead to possible mass manipulation of populace, as has been the case with elections all over the world, the US election of 2016 being the most notable.
With stakes at this high point, consumers are encouraged to be conscious of the level of protection being provided to them by their service providers. Customers of Android can rest easy at night, knowing that the company continues to monitor and invest heavily in outsmarting possible breaches. Google, on a quarterly basis, publishes reports highlighting the changes and improvements being made to its system because what better way to weigh the security level provided by various service providers than quantifiable metrics?
As security threats become more sophisticated, so do service providers. While all providers have been and continue to be invested in providing a safe environment for their customers, our discussion above effectively sums up why Android can be trusted with your more precious commodity, data.
Data breaches
Even though our phones get more secure by hardware default and Safety measures data breaches continue to make the news around the globe. Even though companies invest big amounts of money into security infrastructure and IT-Help-desks, data gets stolen and the reputation of the company gets damaged. Research showed that the costs of a data breach goes into the millions. We recently wrote an article about this topic: Have a look.
Let’s detect the weak spot
The Verizon Data Breach Investigations Report reveals that 80% of hacking-related breaches still involving compromised and weak credentials.
A common problem is that most people use the same password over and over again. The fear of forgetting a password leads to this. Therefore it is no surprise that over 60% say that it is key to remember the password easily and another 39% do not change their password or believe it is not required.
Companies trust in Single Sign-On
With Single Sign-On (SSO) the user only authenticates once through their device – this is enough to identify the user and grant access for all applications in the company.
With SSO your password can be as long and complex as you want – so it is impossible to get your credentials.
To authenticate, Kerberos is the standard protocol. It is using ticket granting system and avoids storing the passwords locally or sending them over the internet. Instead it uses a trusted 3rd-party server (Key distribution Center or so called KDC).
Android Enterprise with SSO
As mentioned before Android Enterprise is a big step forward in many ways. But keep in mind Android Enterprise is lacking Kerberos based Single Sign-On (or Kerberos Constrained Delegation). Which used to work with EMM Proprietary solutions on Device Admin. For those of you who have Kerberos in use in your company, please be informed that at the end of 2019 AER EMM device admin will be deprecated.
To bridge this gap, Hypergate is needed – a flexible solution which is EMM and device agnostic. The application is customizable and implemented in an instant – IT admins will just love it, because no further infrastructural changes are needed.

Hypergate Authenticator is like a Swiss pocket knife: Simple and effective. It acts as a local proxy for token requests and manages Single Sign On keys for all apps. The end-user will never interact with Hypergate directly – No Pop-up and no requests for username and password. Hypergate increases the security, saves time and keeps the great Android user experience we are used to.
Using Android Enterprise versus Device Admin (DA) is recommended for all deployments going forward because:
- Device Admin API’s have been marked deprecated and will not be supported
- Device Admin API’s provided an outdated security model and management approach
- Android Enterprise offers a modern management framework with enterprise APIs and secure app deployment via managed Google Play.
Google recommends that customers migrate from Device Admin-based management solutions to deployments that leverage the more full-featured Android Enterprise framework via an EMM provider.
Questions? Ask us!
If you have any questions regarding Android Enterprise or Hypergate please don’t hesitate to ask. Otherwise we highly recommend you this detailed Android Enterprise FAQ including tips and tricks helping you to be prepared to switch to AE from Jason Bayton.
Switch now to Android Enterprise to be prepared for any security thread in the future.